Penetration test: IT security analyses on the highest level
Pentest: State-of-the-Art in IT System Intrusion
What do we mean by a penetration test (short: pentest)?
We assess the IT security level in your company from two different perpectives: SySS security tests comprise the connection of the internal network with the internet as well as the specific internal infrastructure, thereby covering the most possible range of attack scenarios.
The penetration test: Reason for Founding
SySS and penetration testing are inseparably linked. In 1998, the penetration test was the reason for the foundation of SySS. Today, we are market leader in Germany as well as in Europe in this field. This is why we focus on high-quality penetration testing with highest quality since we started.
The purpose of a penetration test
Which outcomes will be achieved by a penetration test?
- Prevent hacker attacks and system intrusions.
- Protect valuable company data and knowledge.
- Save time and reduce costs in tracing and tracking potential hacker attacks.
- Remain in control over your IT system.
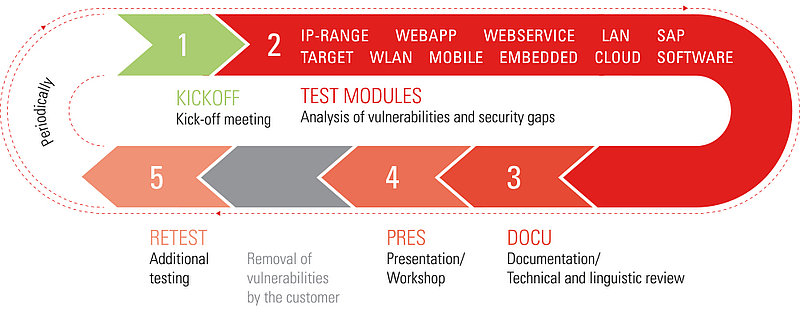
Pentest design
The following diagram illustrates the modular structure according to which we conduct a penetration test. The approach is documented in detail in our White Paper.

You are interested in a penetration test?
We will ensure that you are being taken care of.
Gizem Düzgün will gladly arrange an appointment for you with one of our sales consultants.

Gizem Düzgün
+49 (0)7071 - 40 78 56-6237
anfrage(at)syss.de

You have a short-term demand?
We also offer penetration tests without any lead time. At the customer's request, the project can begin (kick-off meeting) on the day of commissioning, with testing activities then starting a maximum of three days later. Agile penetration testing always takes place remotely and implies that no complex preparation is required.
Docu
For each project carried out, you will receive a detailed written documentation. In this test report, we present the test results as well as a description of the test procedure and the tested objects. Therefore, the documentation serves as a comprehensive basis for the elimination of vulnerabilities. In a two-step quality assurance process, the report is reviewed for technical and linguistic accuracy.
Retest
Given the dynamic nature of IT systems and networks, security risks and gateways change over time. Hence, a penetration test is only a snapshot of the current security standard. If required changes are implemented in response to a penetration test, we strongly recommend an follow-up examination. We thereby determine the security impact of implemented changes on your system and check whether there are any remaining or potential new issues.
IP-RANGE
Analysis of, e.g., your IP address ranges that are accessible via the internet or selected internal systems
LAN
Analysis of your systems from the local network, e.g., "the cleaning staff/intern scenario", client, VLAN, Active Directory analysis, testing of production systems and critical infrastructure
VOIP-UC
Security analysis for Voice-over-IP and Unified Communication .
MOBILE
In-depth security test of mobile apps and devices (e.g., iOS, Android) as well as mobile device management solutions
EMBEDDED
Individual laboratory tests: firmware, hardware and device testing, Internet of Things (IoT) product testing
Cloud
Analysis of your AWS or Azure environment incl. audit of configuration and penetration test
DO NOT HESITATE TO GET IN TOUCH +49 (0)7071 - 40 78 56-0 or anfrage@syss.de | OUTSIDE REGULAR OFFICE Hours CALL +49 (0)7071 - 40 78 56-99
As a framework contract customer please dial the provided on-call service number
DO NOT HESITATE TO GET IN TOUCH +49 (0)7071 - 40 78 56-0 or anfrage@syss.de
OUTSIDE REGULAR OFFICE Hours CALL +49 (0)7071 - 40 78 56-99
As a framework contract customer please dial the provided on-call service number
GET IN TOUCH
+49 (0)7071 - 40 78 56-0 or anfrage@syss.de
OUTSIDE REGULAR OFFICE Hours
+49 (0)7071 - 40 78 56-99
As a framework contract customer please dial the provided on-call service number